Phishing attacks are one of the most common security challenges that both individuals and companies face in keeping their information secure. Whether it is getting access to passwords, credit cards, or other sensitive information, hackers are using email, social media, phone calls, and any form of communication they can to steal valuable data. Businesses, of course, are a particularly worthwhile target.
What is Phishing attack?
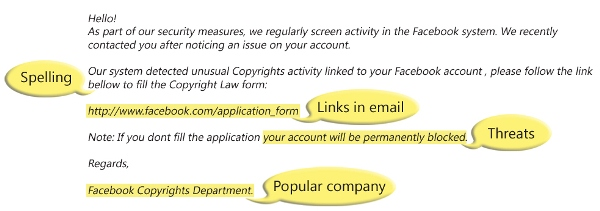
Often posing as a request for data from a trusted third party, phishing attacks are sent via email and ask users to click on a link and enter their personal data. Phishing emails have gotten much more sophisticated in recent years, making it difficult for some people to discern a legitimate request for information from a false one. Phishing emails often fall into the same category as spam, but are more harmful than just a simple ad.
Spear Phishing
Spear phishing is an email spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data.
The spear phisher thrives on familiarity. He knows your name, your email address, and at least a little about you. The salutation on the email message is likely to be personalized: “Hi Bob” instead of “Dear Sir.” The email may make reference to a “mutual friend.” Or to a recent online purchase you’ve made. Because the email seems to come from someone you know, you may be less vigilant and give them the information they ask for. And when it’s a company you know asking for urgent action, you may be tempted to act before thinking.
How does it work?
Phishing emails include a link that directs the user to a dummy site that will steal a user’s information. In some cases, all a user has to do is click on the link.
Example of Phishing Scams: 2003 saw the proliferation of a phishing scam in which users received emails supposedly from eBay claiming that the user’s account was about to be suspended unless he clicked on the provided email link and updated the credit card information that the genuine eBay already had. Because it is relatively simple to make a website look like a legitimate organization’s site by mimicking the HTML code, the scam counted on people being tricked into thinking they were actually being contacted by eBay and were subsequently going to eBay’s site to update their account information.
Why is Phishing Successful for Scammers?
Phishing emails are blindly sent to thousands, if not millions of recipients. By spamming large groups of people, the “phisher” counts on the email being read by a percentage of people who actually have an account with the legitimate company being spoofed in the email and corresponding webpage.
Phishing, also referred to as brand spoofing or carding, is a variation on “fishing,” the idea being that bait is thrown out with the hopes that while most will ignore the bait, some will be tempted into biting.
How to prevent Phishing attack:
- Educate your employees and conduct training sessions with mock phishing scenarios.
- Deploy a SPAM filter that detects viruses, blank senders, etc.
- Keep all systems current with the latest security patches and updates.
- Install an antivirus solution, schedule signature updates, and monitor the antivirus status on all equipment.
- Develop a security policy that includes but isn’t limited to password expiration and complexity.
- Deploy a web filter to block malicious websites.
- Encrypt all sensitive company information.
- Convert HTML email into text only email messages or disable HTML email messages.
- Require encryption for employees that are telecommuting.
- Verify any requests from institutions that arrive via email over the phone. If the email itself has a phone number, don’t call that number, but rather one you find independently online or within documentation you’ve received from that company.
- Most companies are adamant that they will not ask for personal information via email. At the same time, most companies strongly recommend that users not make sensitive information available. While it might seem like a pain to make a phone call to find out if something is legitimate, the hassle of having your Social Security number or EIN stolen is worse.